Overview
Security, only as strong as the weakest link
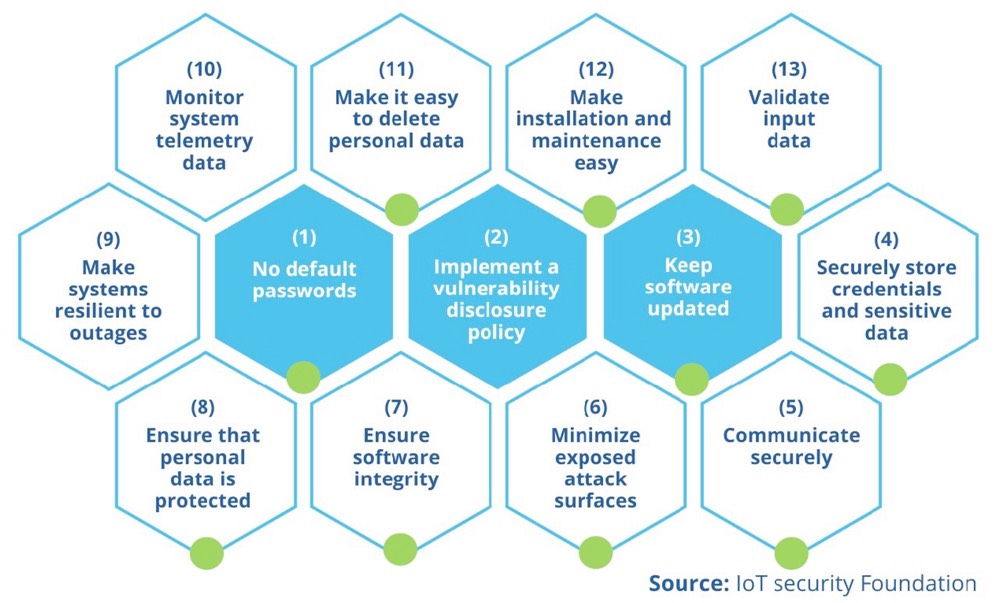
As the digital landscape evolves at an unprecedented pace, the proliferation of interconnected devices has unleashed a wave of unprecedented convenience and efficiency. However, as we revel in the benefits of this interconnected ecosystem, a pressing concern looms large – the critical need for robust IoT security. The significance of IoT security cannot be overstated, from personal information to critical infrastructure controls, the interconnected nature of IoT makes it a prime target for malicious actors seeking to exploit vulnerabilities for various purposes. As we unlock the full potential of IoT, a robust security framework becomes not merely a precautionary measure but an indispensable necessity for ensuring the integrity, privacy, and resilience of our digital ecosystem. IoT security stands as a linchpin in our quest for a secure and connected tomorrow.
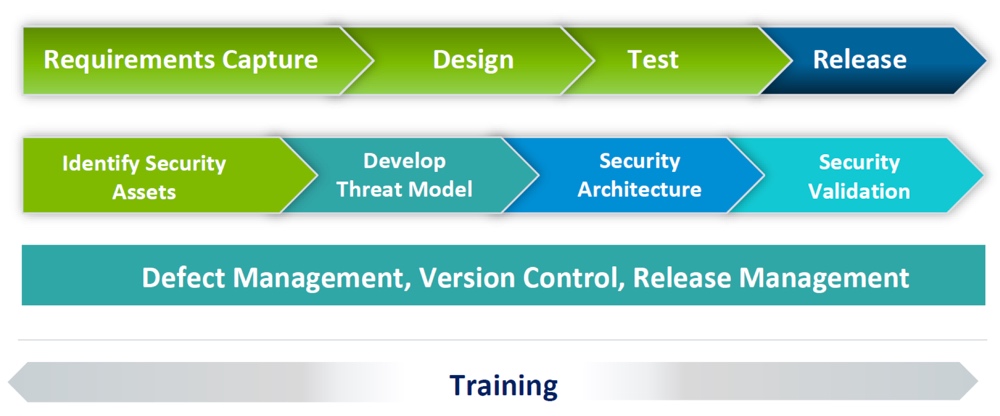
Security By Design
Security Across the full product lifecycle is critical and best security practices are not just recommended but essential in connected device development, deployment and scaling. Below is the SDL process that we follow to ensure security is never and afterthought or bolt-on.